2023. 9. 12. 13:20ㆍ컴퓨터/컴퓨터 구조
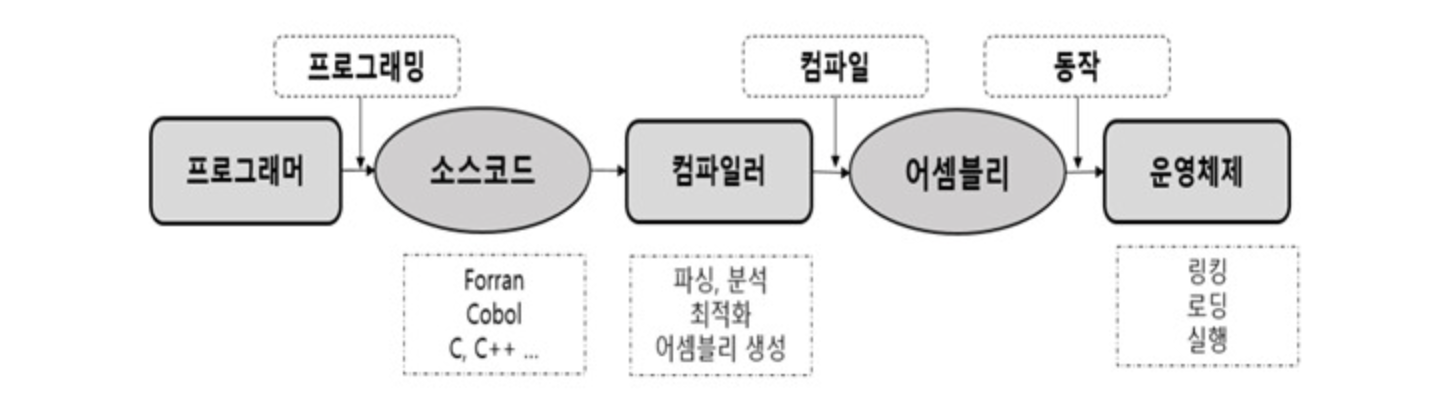
프로그래밍을 할 경우 위와 같은 순서로 프로그래밍 언어는 어셈블리언어, 기계언어로 변환된다. 해킹을 하는데 있어서 단순코드가 아닌 기계언어를 바꿀 경우 해당 파일이 정상적으로 컴파일되거나 실행되지 않을 것이다. 시스템해킹에서 특히 사용되는 기계언어와 컴퓨터구조를 공부해 보려고 한다.
오늘은 각각의 단계에서 언어가 어떤식으로 변환되는지 살펴보려고 한다. 자세한 C언어와 어셈블리언어에 대한 설명은 다음 포스팅에서 진행하려고 한다.
시작하기 앞서 각각의 단계마다 변환된 파일을 리눅스환경에서 쉽게 접근하기 위해 GCC Compiler를 사용하였다.

파일 변환 순서는 main.c -> main.i -> main.s -> main.o 순서이다. main파일은 이전 포스팅에서 사용한 비트연산파일을 재사용했다.
gcc -E main.c -o main.i //전처리 과정
gcc -S main.i -o main.s //컴파일 과정
gcc -c main.s -o main.o //어셈블 과정
main.o는 오브젝트 파일이고 main은 링킹 과정을 거친 실행 파일이다.
- readelf
ELF(Execurable and readable file)은 링킹 과정을 거친 파일
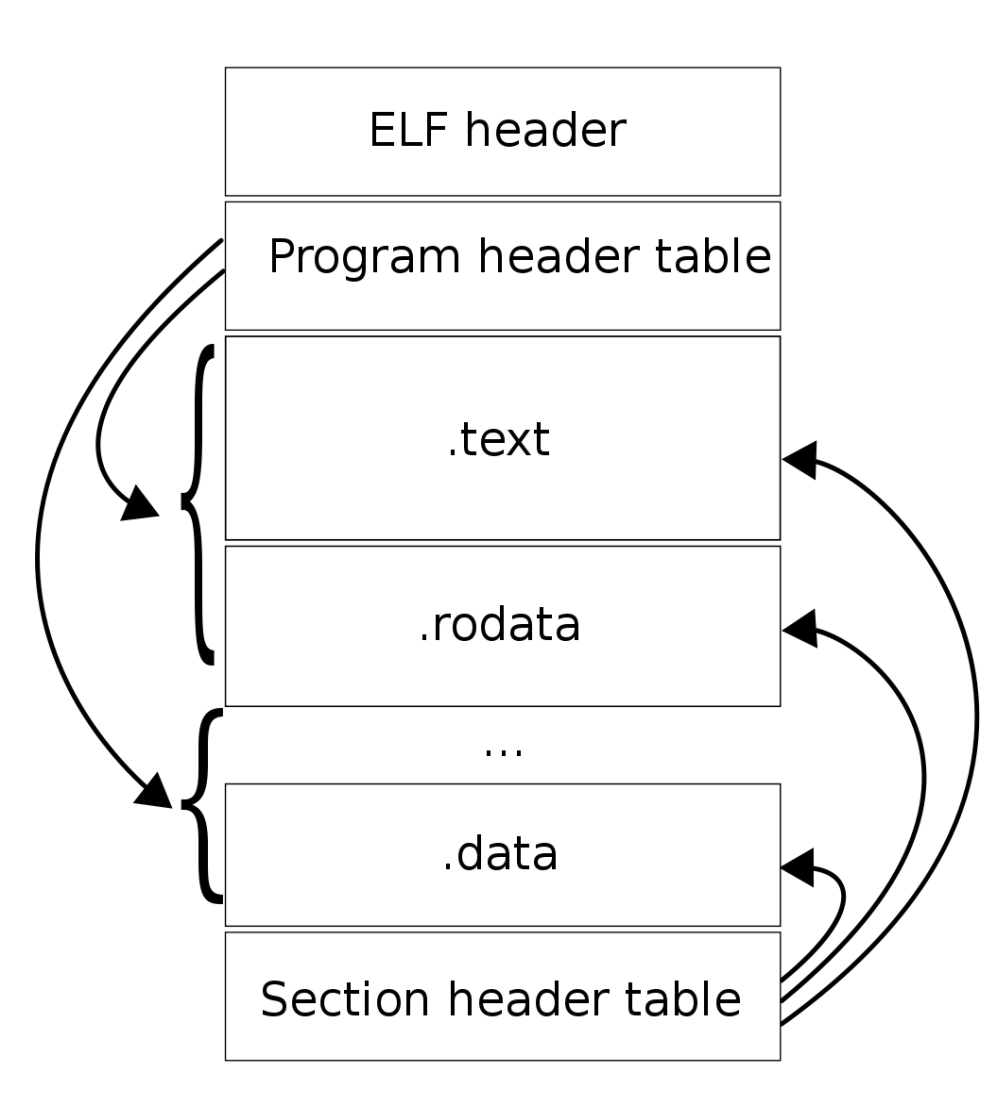
출처: https://people.redhat.com/mpolacek/src/devconf2012.pdf

| ELF Header |
Section Headers |
Section Groups |
Program Headers |
Dynamic Section |
Relocation Sections |
Symbol table | |
| main.o | o | o | x | x | x | o | o |
| main | o | o | o | o | o | o | o |
- objdump

실행파일인 main 파일이 링크되면서 함수 개수가 늘어난 것을 볼 수 있다.
마지막으로 readelf와 objdump의 특징과 차이를 간략하게 정리하기 이해서 chat-GPT를 사용했다.
- what is readelf?
readelf is a command-line utility commonly found on Unix-like operating systems, particularly Linux. It is part of the GNU Binutils package, which provides a collection of tools for manipulating binary files, object files, and executable programs. readelf is specifically designed for examining the structure and information contained within ELF (Executable and Linkable Format) files.
ELF is a common binary file format used on Unix-like systems for executables, shared libraries, object files, and other binary artifacts. readelf is a versatile tool for inspecting and analyzing ELF files, and it provides detailed information about their headers, sections, symbols, and various attributes.
Here are some common uses of the readelf command:
- Display ELF Header Information: readelf can show detailed information about the ELF header, including the file type, architecture, entry point, program headers, and more.
- List Symbol Tables: It can list the symbol tables within an ELF file, which contain information about functions, variables, and other symbols defined or referenced in the binary.
- Show Section Information: readelf can provide information about the sections present in the ELF file, including their names, sizes, and attributes. Sections are used to organize and store data, code, and other information in the binary.
- Display Dynamic Section Information: For dynamically linked executables and shared libraries, readelf can display information about the dynamic section, including shared library dependencies and symbol resolution information.
- Inspect Program Headers: It can show information about the program headers in an ELF file, which describe how the binary should be loaded into memory.
- Examine Relocation Information: readelf can display relocation entries, which are used to adjust addresses in the binary to accommodate changes when linking or loading shared libraries.
- View Version Information: For shared libraries, readelf can display version information, showing which versions of a library are required and provided.
Overall, readelf is a valuable tool for developers, system administrators, and anyone involved in analyzing or debugging ELF files on Unix-like systems. It helps users understand the internal structure and characteristics of these binary files, which is essential for various development and system maintenance tasks
- what is objdump?
objdump is a command-line utility that is commonly found on Unix-like operating systems, including Linux. It is part of the GNU Binutils package, which includes various tools for manipulating binary files, object files, and executable programs. objdump is primarily used for examining the contents of binary files, particularly object files and executables, in various formats.
Here are some of the common uses of objdump:
- Disassembling Code: objdump can disassemble binary code, which means it can display the assembly language representation of a compiled program. This is helpful for understanding how a program works at a low level.
- Examining Headers: It can display information about the headers and sections of an executable or object file, including information about the architecture, symbol tables, and more.
- Inspecting Symbols: objdump can show you information about symbols in the binary, including functions, variables, and their addresses.
- Dumping Data: You can use objdump to dump the binary data in different formats, such as hexadecimal or ASCII, from a file.
- Dynamic Section Analysis: When dealing with shared libraries or dynamically linked executables, objdump can display information about the dynamic sections, including shared library dependencies.
Here's a basic example of how you might use objdump to disassemble a binary file:
This command would disassemble the binary file my_program and display the assembly code for its machine instructions.
objdump is a powerful tool used by developers, reverse engineers, and system administrators to gain insights into the structure and behavior of binary files, making it a valuable utility for low-level debugging and analysis
- what is key difference between readelf and objdump?
readelf and objdump are both command-line utilities used for examining and analyzing binary files, particularly in the context of object files and executables. However, they serve different primary purposes and offer distinct features. Here are the key differences between readelf and objdump:
- Purpose:
- readelf: Its primary purpose is to provide detailed information about the structure and attributes of ELF (Executable and Linkable Format) files. It focuses on displaying the internal structure of the binary and is particularly useful for examining headers, sections, and symbols within ELF files.
- objdump: Its primary purpose is to disassemble and display the assembly code generated from the binary's machine code. It is mainly used for examining the binary's code, including functions, instructions, and control flow.
- Output:
- readelf: It provides detailed textual information about the ELF file's structure, such as headers, sections, symbol tables, and dynamic sections.
- objdump: It generates human-readable assembly code or machine code representations of the binary's executable instructions, allowing you to inspect the code's behavior.
- Usage:
- readelf: Typically used for inspecting and understanding the internal layout of ELF files, such as executable binaries and shared libraries. It's useful for checking metadata, section attributes, and symbol information.
- objdump: Primarily used for reverse engineering, debugging, and code analysis. It helps you disassemble and analyze the actual code and control flow of the binary.
- Common Use Cases:
- readelf: Used for examining ELF headers, section attributes, symbol tables, dynamic section information, and other metadata in ELF files.
- objdump: Used for disassembling executable code, analyzing program flow, investigating machine instructions, and debugging binary programs.
In summary, readelf is focused on providing detailed metadata and structural information about ELF files, while objdump is oriented toward disassembling and analyzing the actual code within those files. Depending on your needs, you may choose one tool over the other or use them in combination for a more comprehensive analysis of binary files
'컴퓨터 > 컴퓨터 구조' 카테고리의 다른 글
| 컴퓨터 구조 실습 [1] (0) | 2023.09.11 |
|---|